Configuring SSO with Azure Active Directory / Entra ID
This page will explain how to enable Single Sign On (SSO) via your Azure Active Directory service and use AD groups to manage roles in KADA. The authentication method used is Open ID connect (Oauth 2.0)
There are 4 keys steps to enable SSO.
This function is restricted to K Administrators
Step 1. Register K in your Azure Active Directory
Log in to your company’s Azure Portal and open the Azure Active Directory page
Select App Registration in the side panel and click New registration
Complete the registration form.
Follow your company’s standard policy for the Supported account types
Leave the Redirect URL blank. We will complete this later
Click on the newly created KADA App
Save the Application (client) ID for use in a later step
Click on Endpoints and save the URL for OpenID Connect metadata document for use in a later step
Select Certificates & secrets in the side panel and click New client secret
Complete the new secret form and save the Secret Value for use in a later stope
Select API permissions in the side panel and click Grant admin consent for [tenant]. This will allow the application to read and authenticate requests
Make sure you’ve saved the following information for easy access in the next process. If a different team is responsible to completing the Keycloak steps, make sure you include the below information in the request.
Application (client) ID
URL for OpenID Connect metadata document
Secret value
Step 2. Connecting K to your Azure Active Directory
Log into to your K platform instance ([customer].kada.ai)
Select Platform Settings in the side bar
In the pop-out side panel, under Administrations, click on Customisation
Under Platform Setup, toggle on Enable Single Sign On
Click on Configure Single Sign On

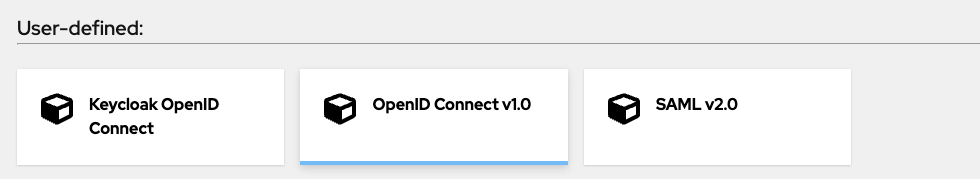
Select Identity Providers in the side panel and click Add Provider
Choose OpenIDConnect v1.0 from the drop down list
Go to Discovery endpoint and paste the URL for OpenID Connect metadata document that you copied in the previous step
Update the following information
Alias - The alias cannot have any characters that require url encoding eg spaces. Copy this name if you plan to only allow SSO identities and disable local user logins.
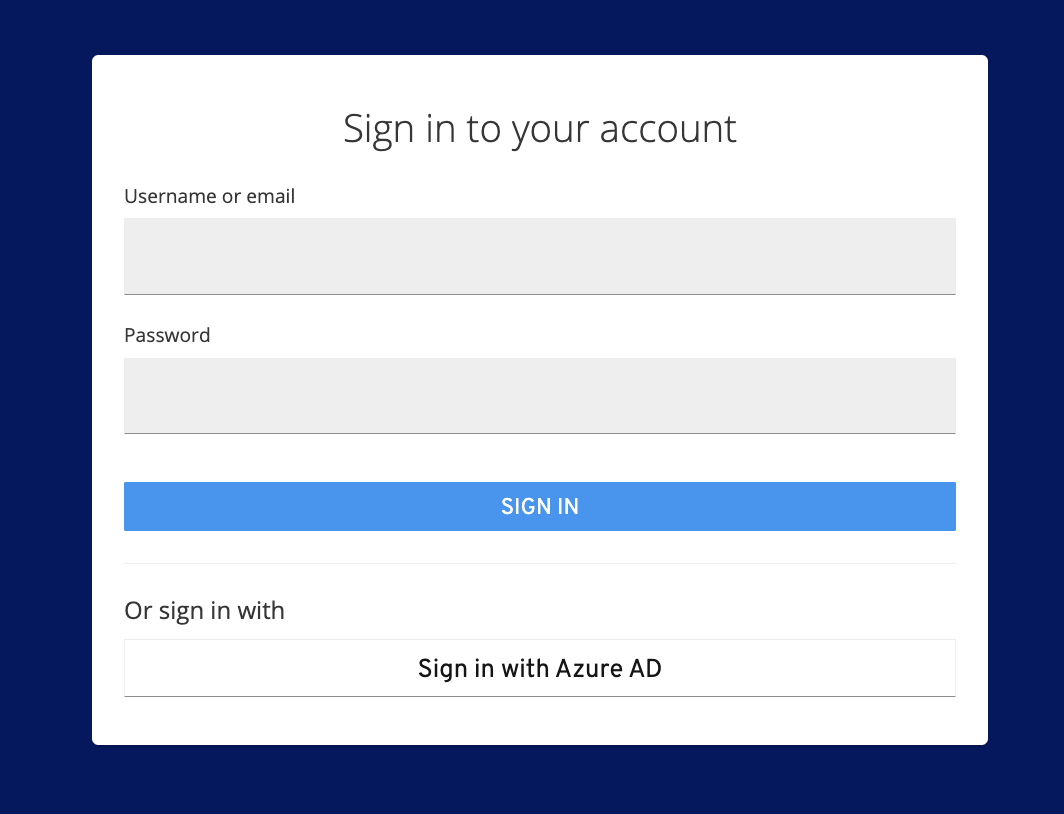
Display Name - This is the name that users select on the Log In page to access via SSO (see below screenshot where the display name was “Sign in with Azure AD”
Client Authentication - Set to Client secret sent as basic auth
Client ID - Paste the Application (client) ID saved from the previous step
Client Secret - Paste the Secret Value saved from the previous step
Copy the Redirect URL for use in a later step
The below Log In option will now appear the next time you try to log in to KADA
Step 3. Complete Azure Active Directory Setup
Log in to your company’s Azure Portal and open the Azure Active Directory page
Select the App Registration tab and open the KADA App you created in Step 1
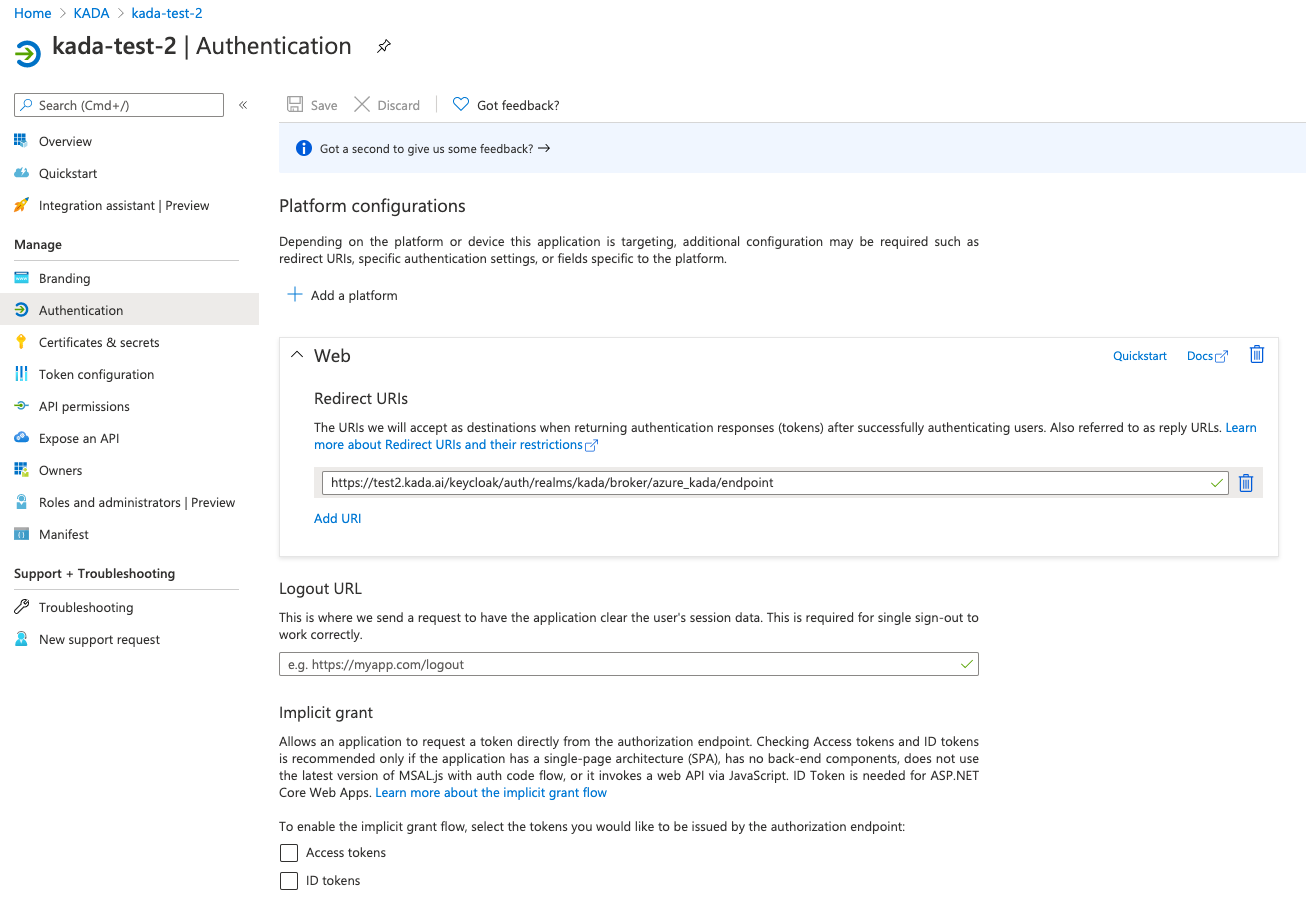
Select Authentication from the side panel and click Add a platform
Select Web, paste the URL Redirect URL you copied when setting up Keycloak and click Save
Step 4. Create AD Groups in Azure
To fully utilise the capabilities of K, we need to create 5 new AD groups in Azure and 5 new roles in the Azure KADA app to align with the KADA role groups:
Log in to your company’s Azure Portal and open the Azure Active Directory page
Select Groups in the side panel and click on New Group. Create 5 Groups that align to the 5 roles In KADA
Administrator
Business User
Data Worker
Data Manager
Data Governance Manager
Select App registrations in the side panel and click on the newly created KADA App
Select App roles in the side panel and click Create app role
Create 5 roles using the information in the following table
Display Name | Value |
|---|---|
Administrator | kada_admin |
Business User | kada_business_user |
Data Worker | kada_user |
Data Manager | kada_manager |
Date Governance Manager | kada_data_gov_manager |
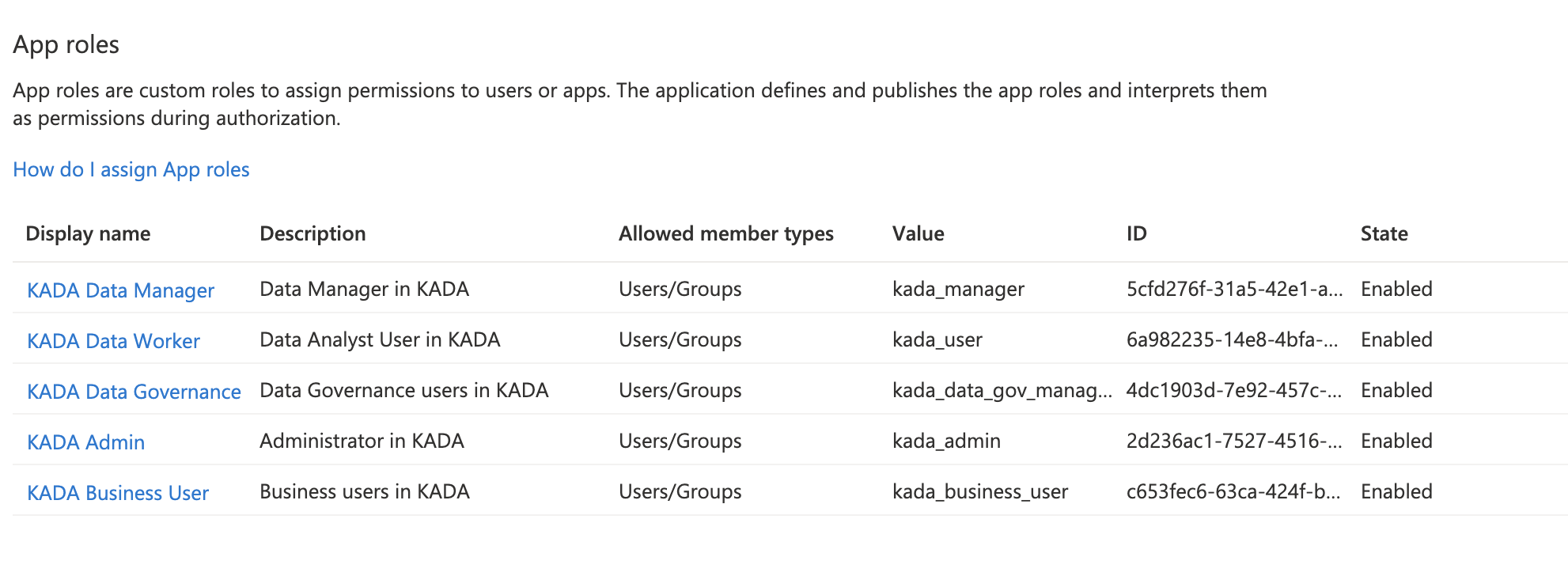
Image of 5 created roles in Azure
Return to the main Azure Portal homepage and open the Enterprise applications page
Select the newly created KADA App
Select Users and groups from the side panel and click Add user/group
Add the 5 groups you created in Azure AD and assign it to the 5 role you created in the KADA app
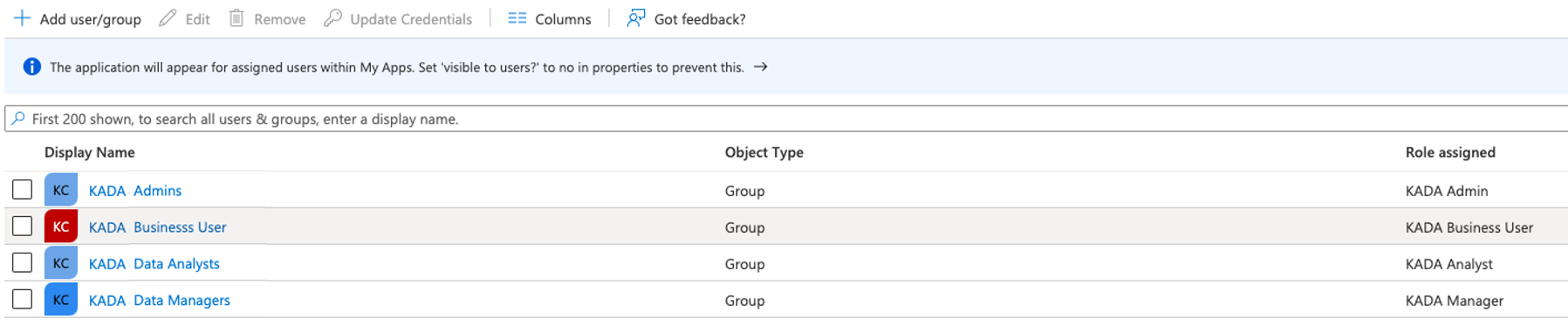
Image of completed group to role mapping
Step 5: Map roles to KADA
We now need to link the roles you created in Step 4 to the roles in the K platform.
Log into to your K platform instance ([customer].kada.ai)
Select Platform Settings in the side bar
In the pop-out side panel, under Administration click on Customisation
Click on Configure Single Sign On
Go to Identity Providers
Select the newly created Identify Provider you created in Step 2 and click on the Mappers tab
You will need click Add Mapper to create a mapping for each role. You will need to complete this step 5 times.
For each role
Set the mapper name: kada_admin_group_mapper
Set Mapper Type to Advanced Claim to Group
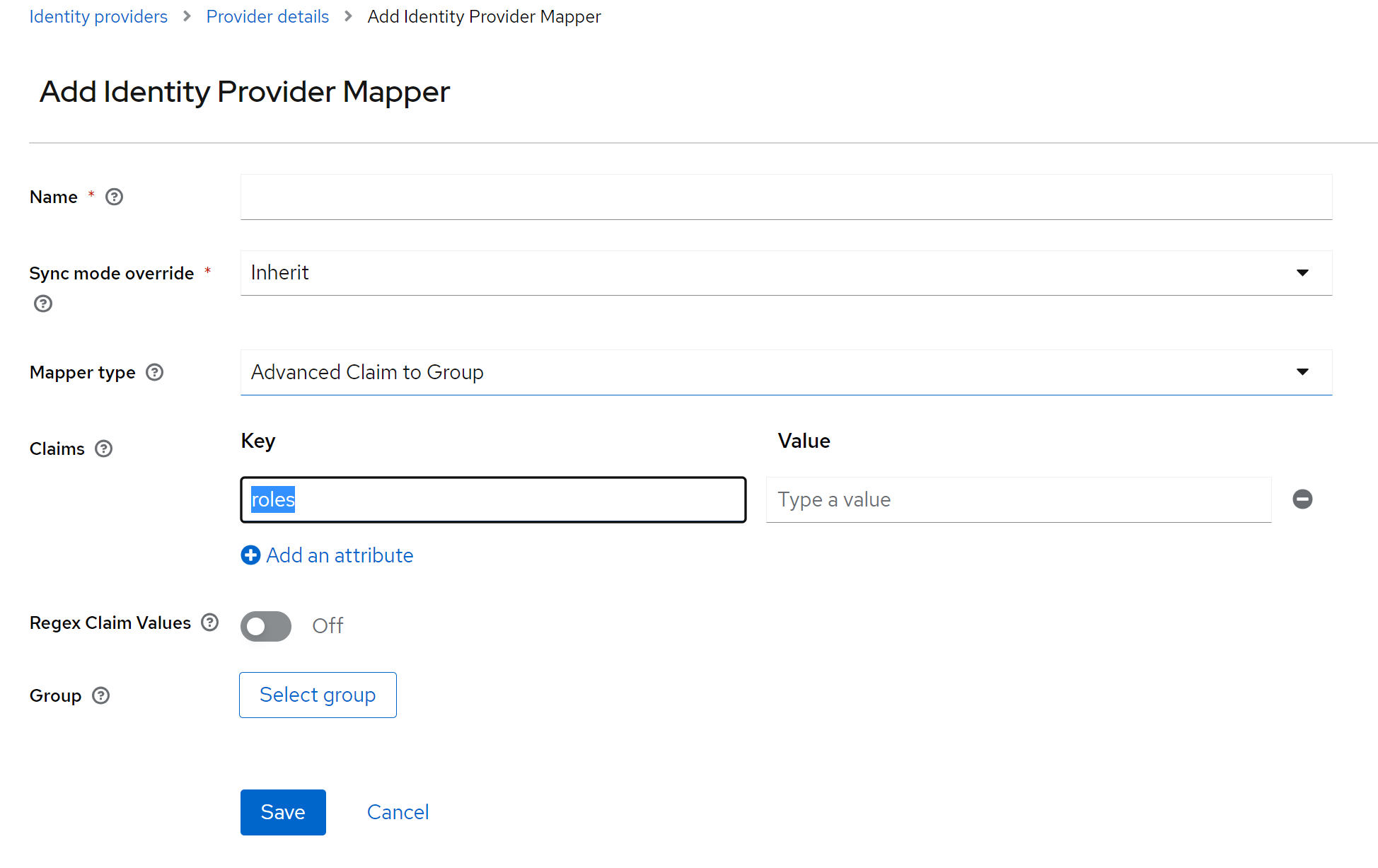
Add roles to the Key field. Add Value from the table below.
For example: For the kada_admin_group_mapper the value is kada_admin
Role Name | Value |
|---|---|
Administrator | kada_admin |
Business User | kada_business_user |
Data Worker | kada_user |
Data Manager | kada_manager |
Data Governance Manager | kada_data_gov_manager |
Check after each mapping is completed. It should look like the below
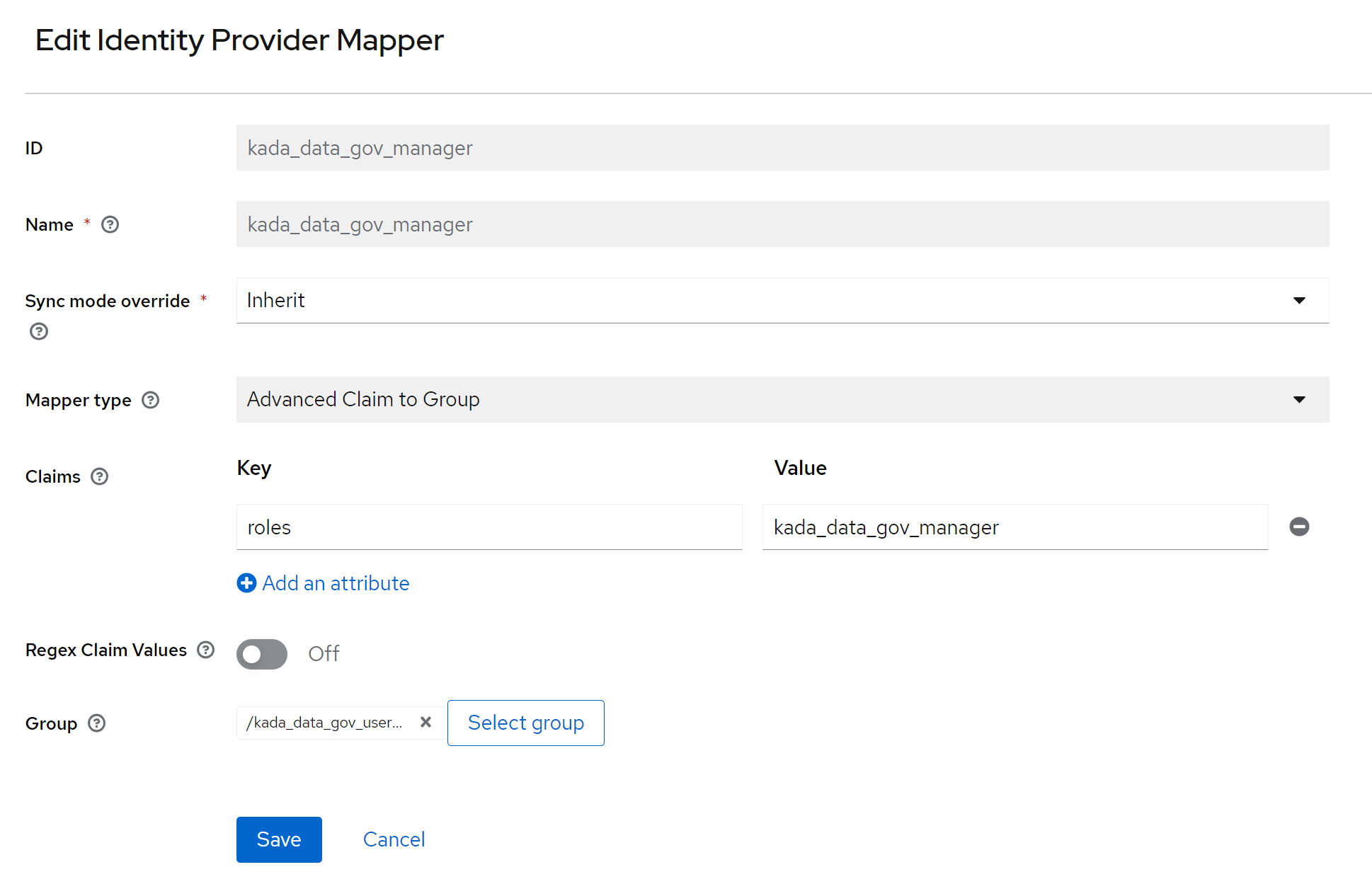
The SSO Setup is now completed. You can now add users to the various AD groups as per your usual processes.
Other information
Enforcing Assignments
To prevent any users from attempting to log into K if they are NOT assigned a K role turn on Assignment required in the K application settings in Active Directory / Entra ID.
Log in to your company’s Azure Portal and open the Azure Active / Entra ID Directory page
Select the Enterprise Applications tab and open the KADA App you created in Step 1
Under the Manage options, select Properties
Enable Assignment required. Click Save

Any user that is not assigned a role will see the following message if they attempt a log into K
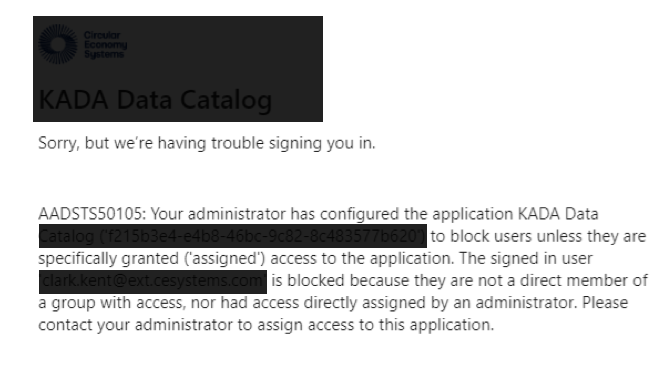
Managing proxies
K uses Keycloak to manage SSO. If Keycloak application is running behind some proxy server then it won’t allow you to import this configuration.
To enable the configuration to be imported, set path for X.509 Client Certificate. Here is link to guide you through this from keycloak.
